Oh boy, technology is great isn't it? From selfies to social media, it's done wonders for us. But with that comes some downsides too. Like the Computer Misuse Act of 1990! Don't worry, I'm here to help you wrap your head around it.
Computer Misuse Act 1990
First up on the list, we have the Computer Misuse Act 1990. Now, what exactly is this act? Basically, it's a law that helps to prevent unauthorized access to computer systems and data. You know, like hacking and all that jazz.

Here's the thing, you might think it's harmless to just log in to someone else's computer or device without their permission, but that can be a violation of this act. And trust me, you don't want to mess with the law, it's not worth the trouble.
What's in the Act
So, let's dive into the specifics of the act. It has three main sections.
Section 1 - Unauthorised access to computer material
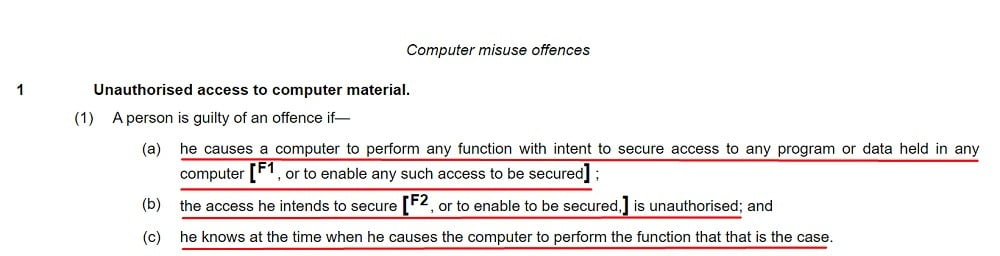
This section essentially makes it a crime to hack or gain access to computer systems or data without proper authorization. Unauthorized access can lead to hefty fines and even prison time.
Section 2 - Unauthorised access to computer material with intent to commit or facilitate commission of further offenses

This section makes it a crime to hack or gain access to computer systems or data with the intent of committing further offenses. For example, gaining access to banking information and using it to steal money. The penalties for this offense can be even more severe than for section 1.
Section 3 - Unauthorised modification of computer material

Section 3 makes it a crime to modify computer systems or data without proper authorization. This can include anything from deleting files to installing malware. The penalties for this offense can also be hefty.
How to Comply with the Act
Now that you know what the Computer Misuse Act is and what's in it, how do you make sure you're in compliance? Here are some tips:
1. Don't Access Computer Systems Without Proper Authorization
This one is a no-brainer. If you don't have permission to access a computer system or data, don't do it.
2. Use Strong Passwords
Using strong passwords can help prevent unauthorized access to your own computer systems and data. Make sure to use a combination of upper and lower case letters, numbers, and symbols.
3. Keep Your Antivirus Software Up-to-date
Keeping your antivirus software up-to-date can help prevent malware from infecting your computer and data.
4. Use Two-factor Authentication
Two-factor authentication adds an extra layer of security to your computer systems and data. It requires you to provide two forms of identification, such as a password and a security token.
Conclusion
Well folks, that's it for the Computer Misuse Act of 1990. I hope this has helped you understand what the law is all about and how to stay in compliance. Remember, it's always better to stay on the right side of the law. Happy computing!