Hey there fellow tech enthusiasts! Today, we're going to talk about the Computer Misuse Act (CMA) of 1990. Now, I know what you're thinking - "Oh boy, a law! This is going to be so much fun!" And let me tell you, it absolutely is!
What is CMA (Computer Misuse Act)?
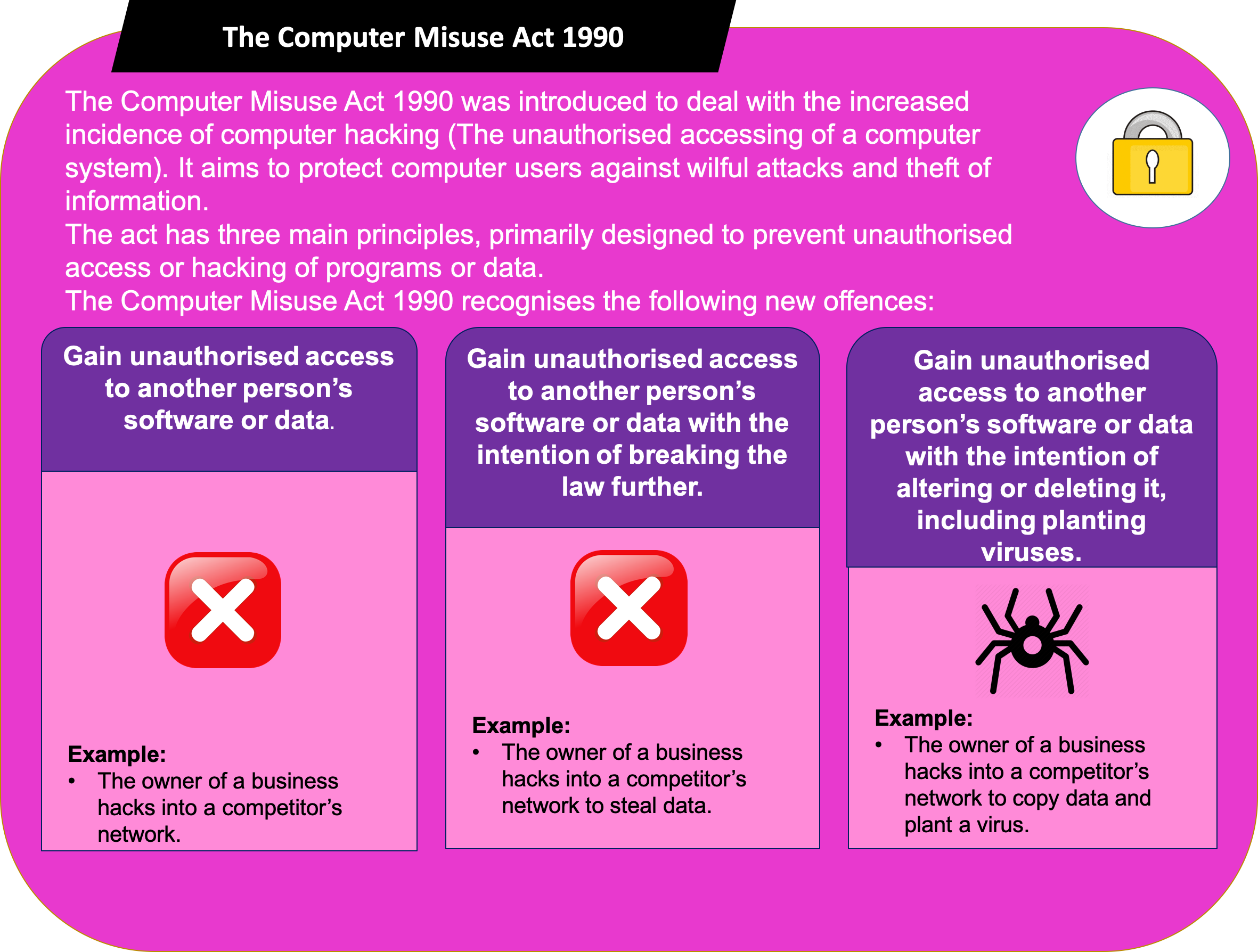
Let's start with the basics, shall we? The Computer Misuse Act of 1990 is a law that was put into place to 'protect computer systems and programs from unauthorized access, modification or damage'. Sounds important, right? Well, it is!

So, what does this mean for us? It means that we can't just go around hacking into other people's computer systems (no matter how tempting it may be). We also can't create, distribute, or use software or tools that are specifically designed to commit computer crimes. Sorry to burst your bubble, budding hackers and cyber criminals!
Ethical, Legal and Environmental impacts of Digital Technology
Now, let's talk about the impacts of digital technology on society. We all know that technology has changed our lives in countless ways - from how we communicate, to how we work, to how we entertain ourselves. But with great power comes great responsibility, as they say.
With the increasing use of technology, there are certain ethical, legal, and environmental impacts that we need to be aware of. For example, the CMA helps to protect our personal data and privacy from cyber criminals who might try to steal it. It also helps to prevent cyber bullying, harassment, and other online crimes.
Cameron Irvine H9HY 46: Computer Misuse Act (1990)
Now, I don't know about you, but I always like to hear about real-life examples of how the law works in action. So, let's take a look at a case study of the CMA in action: Cameron Irvine and the Computer Misuse Act.
Cameron Irvine was a student who was found guilty under the Computer Misuse Act for releasing a virus that caused damage to his college's computer systems. As a result, he was sentenced to a fine of £200 and 100 hours of community service. Moral of the story? Don't mess with the CMA!
Types of Offenses
Now, you may be wondering - what specific types of offenses are covered under the CMA? Well, let's take a closer look.

The CMA covers a wide range of offenses, including unauthorized access to computer systems, unauthorized modifications to computer programs or data, and the creation or distribution of tools that are designed to commit computer crimes. So, if you were thinking about trying to hack into your ex's Gmail account, you might want to think again!
Penalties for Offenses
Okay, okay, so you might be thinking, "What's the big deal? It's not like anyone's actually getting caught and punished for these crimes." Well, my friend, you couldn't be more wrong!

The penalties for offenses under the CMA can be pretty steep. For example, the maximum penalty for unauthorized access to a computer is currently 2 years in prison or a fine (or both). The penalties for other offenses, such as the creation or distribution of tools for committing cyber crimes, can be even more severe.
Why the CMA is Important
You might be thinking, "Okay, so there are all these rules and penalties and stuff, but why does it really matter? Why should I care?" Well, my dears, I'm glad you asked.

The truth is, the CMA is incredibly important for protecting our personal data and privacy. With the increasing use of technology in our daily lives, it's more important than ever to make sure that our information is secure and that cyber criminals can't just waltz in and steal it.
How to Stay Safe and Legal
Now that we've covered all the nitty-gritty details of the CMA, you might be wondering - how can I make sure that I'm staying safe and legal?

Well, there are a few things you can do to make sure that you're not breaking any laws or getting yourself into trouble. First and foremost, always make sure that you have permission before accessing someone else's computer or personal data. Second, don't use or distribute software or tools that are designed for criminal purposes. And finally, make sure that you're always following best practices for secure online behavior, such as using strong passwords and keeping your software up to date.
So there you have it, folks - the Computer Misuse Act of 1990 in all its glory! Now go forth and use your tech powers for good (and legal) purposes!